Real Stories: How Volunteer Management Software Transformed Hospice Programs
Volunteers play a crucial role in hospice programs, offering compassion, support, and companionship to patients and their families. However,...
Over the past three or four decades, the way we lead and support our volunteers has changed dramatically. What began as a something of an art form job to effectively connect with those willing to give their time for free has evolved into being a profession with new priorities that required new skills to be honed.
According to Andy Fryar, this ‘evolution’ has had two significant stages:
In this later stage, engaging volunteers had a stronger focus on policy and procedures, and the management of volunteering data started to move from paper-based applications to computers. In the ensuing 20 years, there have been many more developments, with most agencies now adopting some kind of electronic database system to lead, support and recruit their volunteer teams.
To keep up, Volunteer Managers had to develop a whole new skill set as new volunteers are recruited online; as vacancies in the schedule are filled directly by volunteers themselves on a website or a mobile app; and as much communication with their teams now occurs remotely.
As providers of Volunteer Management software, we are in a privileged position to work with agencies of all shapes and sizes on a daily basis. And for the most part, organisations that engage volunteers and choose to adopt Volunteer Management software understand that the security of the volunteer data they are entrusted with is critical. They understand that information can be stolen and that handling confidential information comes great responsibility. For those in larger agencies, it is good to see many have access to an IT team or Privacy Officer who can assist them as they make important decisions about data handling and storage.
Conversely, we have also witnessed some terrible practices! These practices, in a worse-case scenario, could lead to lawsuits and potentially a catastrophic loss of reputation for the organisation that the volunteer manager works for.
While merely being aware that data should be kept private and treated with sensitivity is all well and good, just how much do Leaders of Volunteer Engagement really know and understand about the ins-and-outs of data handling and integrity? Do we rely too much on others to advise us correctly?
In the interests of providing a continual ‘evolution’ of knowledge, we offer the following thoughts and observations to help you think through your own practices and determine whether there might be room for improvement.
In this article, we are not only referring to the volunteer management software you have chosen or are considering; the points we raise in this article lend themselves to be true when considering any software or system you choose to engage with that will handle information of sensitivity.
On one hand, the old adage of ‘you get what you pay for’ can largely ring true when purchasing any software, and more often than not, anything made freely available will likely come with some catches. While this is not always true, it is important to review and weigh up the licencing agreement of any software when considering a purchase and not rely on price alone.
Some questions to consider at this early point might include:
It’s important to remember that whatever solution you land on is going to be the carriage for the private and personal details of your entire volunteer team, so weighing up the few dollars you might save against the catastrophic consequences of a data breach, is an important first step.
Remember too, that those companies that charge for their services will potentially have a greater ability to re-invest in higher levels of security to protect your data.
In the world of data privacy and all things related to the internet, there are many certifications pertaining to data security and privacy that companies who provide software can attain. Some of these are of more importance than others – while some don’t mean much at all.
There are several certifications that can provide assurance that an organization is doing everything right with data privacy and security. One that stands out of the pack and is of global repute is an ISO Certification, so that will be one of the first things you will want to look for.
Also, don’t be afraid to ask any prospective vendor to explain what their certifications mean if this is not clear to you. After all, you’re a Volunteer Manager and not an IT or privacy expert, so ask them to explain this information to you in plain language.
Equally, a prospective vendor who has no certification at all may just be signalling to you that they have very little commitment to their company’s own continual improvement and the data being held on behalf of their clients.
Another term to become familiar with is encryption.
Encryption essentially determines how your data can been seen and interpreted if intercepted by hackers. Essentially, encrypted data appears ‘scrambled’ to any hacker and is of little to no use to them. But did you know there are two types of encryption?
While most websites and software offer the encryption of data while in transit – that is, while it is being moved from one place to another online – there’s a second and equally important type of encryption called encryption at rest. Encryption ‘at rest’ simply means that if your database was broken into while your data was not in transit, the data will continue to appear in this ‘scrambled’ and unreadable state.

We’ve already talked about how reputable software companies will be able to quickly and easily demonstrate that your data is safe and secure, and that they will have an ongoing and transparent commitment to continual improvement when it comes to these important topics.
So, why shouldn’t the same be true for you, your volunteer program, and the agency you work or volunteer in?
We will talk in the next section about the policies and procedures you might like to consider putting in place. But policies and procedures are, quite frankly, next to useless if you don’t have an overarching commitment to the ongoing development of your security practices and the training that surrounds that.
Unfortunately, when it comes to security and privacy, it’s not simply a ‘set-and-forget’ action or a one-time conversation with your IT team.
As new technology comes to hand, as new hacking threats appear, as new certifications and local legislations change, and as new rumours surface, we need to be committed to continually improving and communicating those practices we have in place for our volunteer program and within our broader agency.
Having a statement of commitment around how we deal with our volunteer data – and entrenching this into our organisational culture, handbooks, volunteer induction and training – is paramount to ongoing success.
A key part of any overarching commitment to better securing the private information you hold about your volunteer team is the action of being pro-active and planning ahead whenever possible. Attend seminars or meet regularly with your IT advisors to learn about the latest threats and the practices you can be putting into place for continual improvement in this space.
All of this leads to you, the Leader of Volunteer Engagement, having greater peace of mind!
With volunteers today being much more tech savvy and aware of their rights when it comes to privacy and data security, selecting systems that enable you to provide clear and succinct answers to the questions and concerns your volunteer team may have around this topic is an important consideration.
There are many elements to safeguarding the private information that you hold about your volunteers. So here’s a starter list of those more common items you will absolutely want to ensure you have considered or put into place for your team.
Passwords – Carefully consider the passwords that you use to access your data. Ensure that they are long, complex, contain a good variety of upper and lower-case characters and are not easily predicted (e.g., Your pet’s name!) Also, mix it up! Ensure that you don’t use the same password for everything and even consider using pass phrases. As you can see by the chart below, password length and complexity change the time it would take for a computer program to figure out your password. Where you have a multitude of passwords to remember, a subscription to a password vault (like 1Password) can be a great investment.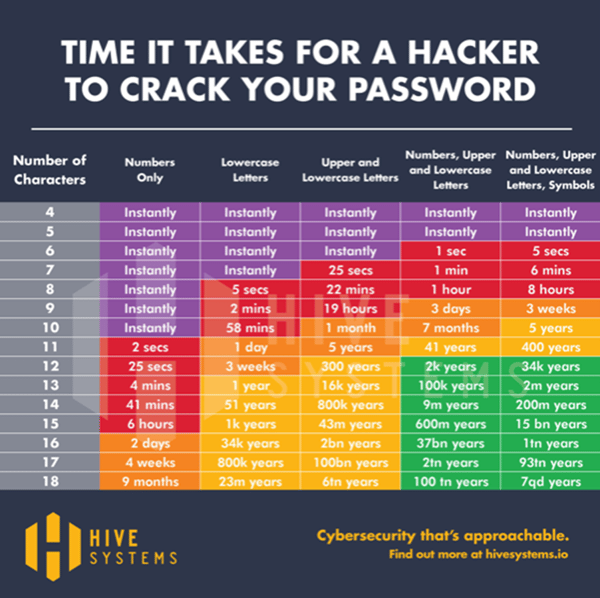
Two or Multifactor Authentication (2FA/MFA) – This is one of the security ‘buzz words’ you’ll hear a lot at the moment. It essentially means that when you log into your system, that you are required to verify your log in on a second device that only you should have access to (like a mobile / cell phone). This makes it harder for those who may get access to your password to log-in – as they’d need the secondary device as well. We would always recommend using a 2FA process where available.
Brute Force Protection – Here’s another security feature that you may have come across, and one you should ensure is in every system you use. Brute force related to passwords is simply a computer program running through every possible password until it finds yours. As you can see in the chart above, if you use a seven-character password with just upper- and lower-case letters, it will only take a modern computer 22 seconds to try enough combinations to find yours. Brute Force Protection stands in the way of this, by making it possible to only a limited number of passwords before being temporarily held back from trying any more. In some cases, a system may lock you out entirely until an administrator reopens the account.
System Access – Carefully consider who has access to your data:
How many? In the same way that too many cooks can spoil the broth, too many administrators in your database systems can lead to a myriad of issues. One key problem we observe from time to time is that access is given to a wide range of admins who invariably move on from their role – and where their access to the software is never removed; in theory, this means they still have access to your team’s private details. Carefully assessing who should have access, keeping those number to a minimum and having sound ‘removal’ processes in place are simple but important steps to take.
Conversely, having too few admins has issues, too. We’ve all seen ‘gatekeepers’ who restrict access to anyone but themselves, leaving the volunteer program and organisation at risk should that person ever get sick, take leave or get hit by a bus! A minimum of two people with access is always a sound policy decision.
Levels of access – Not all administrators are equal. Ensure that your administrators only have access to the areas of the software that they need to have access to. This can be a particularly hazardous issue where administrators who believe they are IT experts suddenly get their fingers into the configuration or settings area of your software and make unsolicited changes which affects all users.
Data minimisation – The principle of data minimisation is a sound and important one. Many volunteering leaders have an innate desire to capture absolutely everything they may ever need to know about an applicant volunteer at stage one of the application process! Not only does this make the application process long and convoluted, in many places it may contravene local legislation or organisational policy.
The principle of data minimisation essentially says we should only ever collect and hold information about our volunteers that we need to know, in order for them to be able to undertake their work for us – and we should only ever collect information at the point we actually need it. Furthermore, we should dispose of it at the point where we no longer have a need to retain that data.
One of the more common occurrences we see are volunteer involving organisations collecting emergency contact details from brand new applicants – even before they’ve had a chance to assess the application and decide if they would like to proceed with the volunteer’s application or not! Once a volunteer leaves your agency, fields like this should be removed from the volunteer record, as it is no longer needed – and should not be kept by your agency.
Transfer of data - Email is simply not a safe or secure way of transferring personal information, and yet it is one of the more common errors we encounter! We’ve even witnessed personal details of volunteers being shared in social media forums! Always ensure that the data you need to pass on is done securely via secure shared folders like Dropbox or ask the vendor of the software you are using how they recommend doing this – as many have their own internally built mechanisms to allow transfers in a safe and secure environment.
Spreadsheet usage – When accessing and using spreadsheets that contain personal information, again ensure that these are stored in secure document folders and not left on your desktop. When it comes to time that you no longer need that spreadsheet, always delete the contents from the spreadsheet and hit save before sending it to the electronic trash bin. If you try to protect your spreadsheets with a password, it is worth noting that there are commercially available products that, in many cases, can readily get around the password protection in a spreadsheet.
Remote log-ins – The pandemic has meant that many more of us are now working not only from home but also from the local coffee shop, library, park or hamburger joint! When accessing your secure database applications in remote locations like this, it’s particularly important not to log into any ‘public and free’ Wi-Fi networks as these are much less secure than those we use in our homes and offices. If you do want to work remotely like this, we would recommend tethering off your personal phone which has the appropriate security settings in place.
Time Out Practices – Another important consideration is to consider how publicly accessible your data might be if you wander away from your desk for any amount of time and don’t shut down access to the data. Being aware to close any secure information when leaving your computer or using the security settings in your software to shut down after a few minutes of inactivity are both good ways to safeguard your private information.
Incident response plan and policy – Sadly, the very best of planning can still see a data or security breach occur. With the amount of malicious malware out there these days, you also need to have a plan in case of this eventuality. If you manage a volunteer team in a larger organisation, chances are there’s already a plan in place – but do you know what it says or what actions you need to take to inform your volunteers should a breach ever occur? For readers operating in smaller organisations, this may be something you’ve never given attention to – but as the volunteer team in many small not-for-profits make up the vast majority of the workforce in those same agencies, it may be time to give some consideration as to what your action plan would be – and be ready to communicate that to anyone who asks.
Security communication channels – Another great strategy is to develop a dedicated channel of communication through which your volunteer team can alert you to any potential security concerns they notice in the course of their volunteering. This keeps the pipeline clear and ensures that issues can be easily raised and quickly acted upon.
Sharing Data – Finally, just because a volunteer has signed up to help your agency, does not automatically mean that you should be sharing their address, phone number or email address with all the other team members they work with. The same applies to their full name! Carefully consider how you share schedules and rosters with your team and gain the appropriate permissions you need before doing this.
While having good policies and procedural practices in place is important, it’s equally important to consider the training that you might provide to your volunteer team about safeguarding their personal details – and particularly to volunteer team members who may assist you in roles where they have access to personal or private information in roles such as:
There are a raft of potential topics that you can include in such training, which may include but not be limited to:
What is most important is that you don’t assume your team understand these things – it is an ongoing journey - and as security and privacy issues continue to grow and morph, so too must the training we provide.
Depending on the size and scope of your organisation, it may also be well worth exploring how your agency would be affected if there ever was a data security breach, and the personal details of your volunteers were leaked. In short, if you were to be sued, where would your agency stand from an insurance perspective?
In this day-and-age, cyber security is a common offering and it may be worth understanding how this may play out in your organisational context.
You should ensure that any platform holding personal data has its own cyber insurance as well.
So, there you have it – a Volunteer Manager’s guide to data privacy and security!
We do hope that this article begins the process of arming you with the necessary information you need to ask the right questions, identify gaps in your current practices and policies and, ultimately, to allow you and your team to operate in an environment where risk in minimised.

Andy Fryar works as the National Operations Manager for volunteer management software company Better Impact across the Australasian region. He is also the Founder and Director of OzVPM (Australasian Volunteer Program Management) - a training and resource company specialising in volunteerism – particularly as it relates to the Australasian region. Over a career in volunteer management spanning more than 30 years, Fryar has worked in a variety of areas involving volunteers, including healthcare and disability services. He has also started and operated a wide variety of social enterprises.

Tony Goodrow is the CEO of Better Impact (www.BetterImpact.com), creators of the volunteer management software - Volunteer Impact - and producer of the annual Volunteer Management Hybrid Conference. In addition to working with volunteer software clients on five continents, Goodrow is a Rotarian and was the founding Chair of the Carpenter Hospice in Burlington (Ontario, Canada). He has been recognized by the Ontario Ministry of Citizenship and Culture, and received the June Callwood award for volunteerism in hospice care. Goodrow has presented on a variety of topics at conferences on volunteerism in Canada, the United States, the United Kingdom, Australia, Brazil, Colombia, Guatemala and Mexico.

Adeyinka Jegede is a multi-talented and highly-skilled business analyst, data privacy engineer, GRC and Information Security Management System consultant with over 18 years of experience providing enterprise leadership in the financial and IT service industries. As compliance and systems specialist at Better Impact, he leads the IT Governance and Information security management services across North America, Europe, Australia, and New Zealand. His expertise in developing world-class information security management systems is evident at Better Impact; in 2021, he led the organization to obtain the globally recognized ISO 27001 and ISO 27017 certifications.
Featured Posts

Volunteers play a crucial role in hospice programs, offering compassion, support, and companionship to patients and their families. However,...

Building a volunteer program isn’t easy, but it may be simpler than you might think. There are five key aspects of a strong volunteer program:...